When you send a financial report to your co-worker via Slack or email this data is considered to be in transit also called data in motion. An example here would be a theme park that uses wristbands to collect data about their guests.
An example here would be a theme park that uses wristbands to collect data about their guests.
Data at rest vs data in motion. Outshine The Rest In Sensual Styles The Latest Trends. Ad Indulge In The Latest Fashions Find Your Next Favourite At Victorias Secret Online Now. Ad Indulge In The Latest Fashions Find Your Next Favourite At Victorias Secret Online Now.
If you often find yourself working from airports cafes and other public places you might be exposing yourself to even greater risks. While streaming analytics for data in motion is now becoming more relevant in todays increasingly data-driven era one should not discount the importance of historical data that can be used to provide deeper insights and more accurate predictions. And theres a batch of data youve taken a certain point in time.
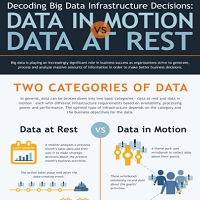
Data at rest refers to information that is stored on a laptop hard drive or other. WORKLOAD REQUIREMENTS Viewing data through the lens of one of these two general categories at rest or in motion can help organizations determine the ideal data processing method and optimal infrastructure required to gain actionable insights and extract real value from big data. Data at Rest vs.
TWO CATEGORIES OF DATA Data in Motion Data at rest refers to information that has been collected from various sources and is analyzed after the data-creating events have occurred. In this case the analytics occur in real-time as the event happens. Denial-of-service attacks website defacement theft of credit card numbers identity theft viruses and worms DNS attacks network penetration and so on.
Outshine The Rest In Sensual Styles The Latest Trends. However the difference lies in the analytics. Applications like data in motion and algorithms used to protect data in motion are also not suitable for use in the data at rest context.
Data in motion is data that is actively being used by data centers it is data in transit. Data in motion vs. For a while now Ive pointed out that cryptography is singularly ill-suited to solve the major network security problems of today.
When it comes to data in motion or data at rest you shouldnt choose one over the other. Data at rest is data that is not being actively used but is stored in a data center. Data in motion refers to information that is actively in transit from one location to another such as an exchange of phone calls texts and emails or data transferred from a local device to a cloud storage device.
The best way to secure data in use is to restrict access by user role limiting system access to only those who need it. Of course the more people and devices that have access to the data the greater the risk that it will end up in the wrong hands at some point. These wristbands would constantly record data about the guests activities and the park could use.
However the difference lies in the analytics. So data at rest is data that youve pulled out of the stream of data thats moving at the speed of customer interactions with your product or service. The collection process for data in motion is similar to that of data at rest.
In this case the analytics occur in real time as the event takes place. So the data and rest idea well maybe I just define these terms first. We recently received a question from a client completing their cyber liability coverage questionnaire which asked.
Data at rest are somewhat self-explanatory but their nuances and impact on data centers are not. Protecting data at rest is far easier than protecting data in use -- information that is being processed accessed or read -- and data in motion -- information that is being transported between systems. Indicate whether the Applicant encrypts private or sensitive date while at rest in the Applicants database or on the Applicants network.
Data in motion The collection process for data in motion is similar to that of data at rest. Data in motion and data at rest. Networks being one of the most vulnerable points in a system the data should be protected while it is motion.
Data in motionrefers to the data being shared or transmitted from one location to another. Data in use is more vulnerable than data at rest because by definition it must be accessible to those who need it. Data sought by law enforcement can be generalized into two broad categories.
It travels by Wi-Fi fiber connection or cellular networks.
